How to Protect Yourself from Crypto Ransomware Attacks
The best way to avoid ransomware attacks is to be aware of them and to take the necessary precautions to protect yourself. The most important thing to do is to make sure that your computer is up-to-date and has the latest security software installed. You should also keep a backup of your data and make sure that you have a back up plan in place in case your computer is damaged or lost.
If you do become infected with ransomware, the best way to protect yourself is to pay the ransom. Ransomware authors are often willing to let users decrypt their files if they pay the ransom. However, be aware that paying the ransom may not guarantee that you will regain access to your data. Often, ransomware authors will only decrypt files if the ransom is paid in full. Therefore, it is important to be cautious and to research ransomware before paying it.
What is Crypto Ransomware and How Does It Work?
Crypto ransomware is a type of malware that encrypts files on a victim's computer, asking for a ransom in order to decrypt them. The malware typically spreads through spam email or malicious links, and once installed, it will begin encrypting files on the victim's computer. If the victim fails to pay the ransom, the malware will delete the encrypted files.
Recent Crypto Ransomware Attacks and How to Remove Them
Crypto ransomware attacks have become increasingly common in recent months, with victims often having to pay ransom to regain access to their data. Here we take a look at some of the most common ransomware strains and how to remove them.
CryptoLocker
CryptoLocker is one of the most notorious ransomware strains, with variant variants typically encrypting files on victim’s computers before demanding a ransom payment in order to decrypt them. The virus was first seen in late 2013 and has since been used to attack tens of thousands of victims.
There is no specific cure for CryptoLocker, but removal of the virus can be done using standard anti-virus Removal tools. In some cases, paying the ransom may be the only way to regain access to the encrypted files.
WannaCry
WannaCry is another well-known crypto ransomware strain, with variants typically infecting users through emails containing malicious attachments. Once installed, the virus locks down infected machines by encrypting files with a custom encryption algorithm.
To remove WannaCry, users will need to install the appropriate anti-virus software and then use its tools to scan for and remove the virus. In some cases, paying the ransom may be the only way to regain access to the encrypted files.
Petya/NotPetya
Petya and NotPetya are two of the most recent crypto ransomware strains, with both variants typically infecting computers through malicious emails. Once installed, the viruses encrypt files on infected machines before displaying a message demanding a ransom payment in order to decrypt them.
To remove Petya or NotPetya, users will need to install the appropriate anti-virus software and then use its tools to scan for and remove the virus. In some cases, paying the ransom may be the only way to regain access to the encrypted files.
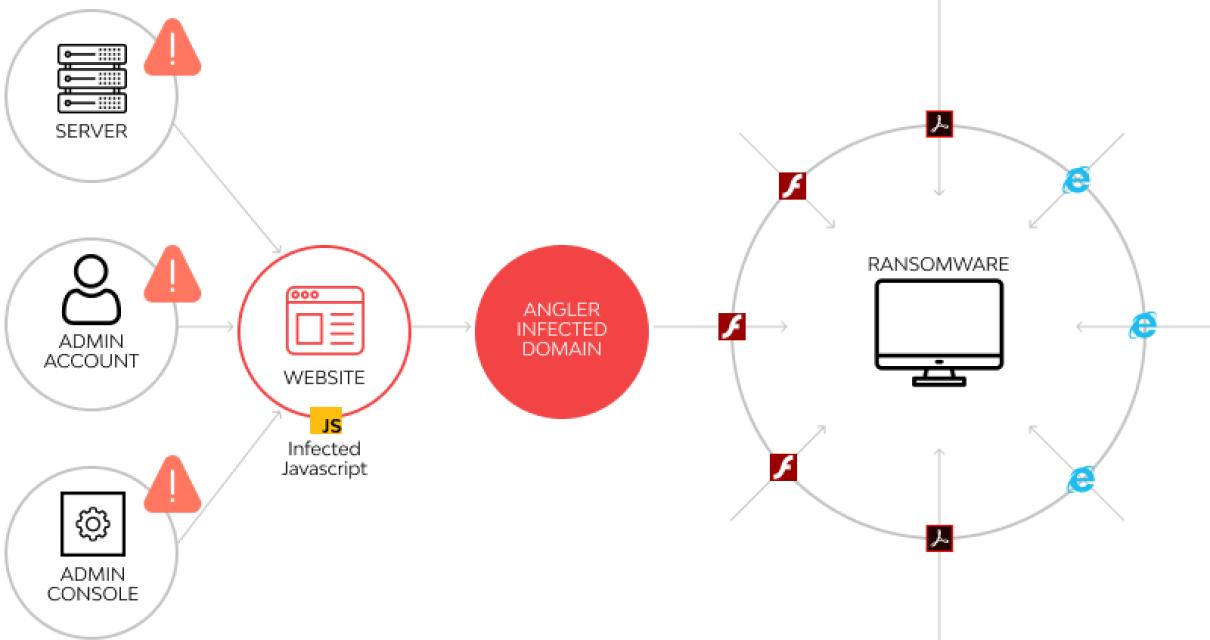
How to Remove Crypto Ransomware Attacks and Protect Yourself
Crypto ransomware attacks are becoming more and more common, and as a result, there are a few things that you can do to protect yourself from them.
The first thing that you should do is make sure that you have up-to-date antivirus software installed on your computer. Crypto ransomware attacks are often delivered through email attachments, so make sure that you always use caution when opening unknown emails.
Another thing that you can do to protect yourself from crypto ransomware attacks is to create a strong password for your computer. Make sure that your password is at least 8 characters long and contains a combination of letters, numbers, and special characters.
Finally, be sure to regularly back up your computer files. If you ever experience a crypto ransomware attack, you can restore your computer files from the backup that you created.

What is Crypto Ransomware and What Are the Recent Attacks?
Crypto ransomware is a type of malware that encrypts files on a victim's computer, making them inaccessible until the user pays a ransom. The recent attacks include the WannaCry and NotPetya ransomware strains, both of which caused widespread damage and affected millions of users.
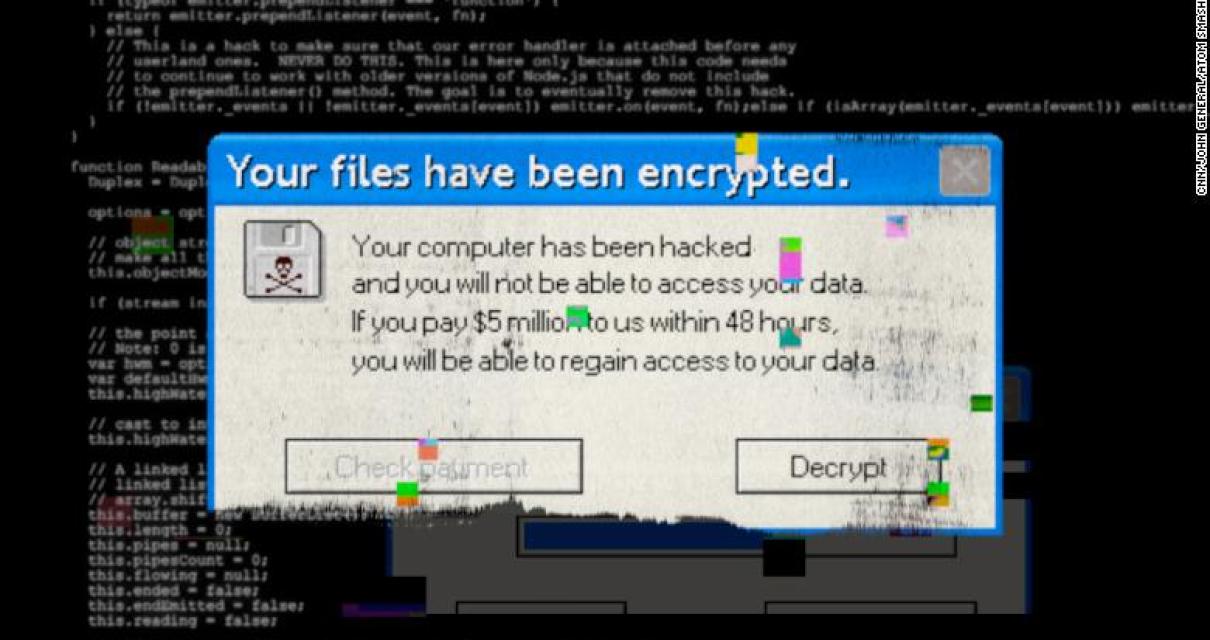
How to Remove Crypto Ransomware and Protect Your Computer
The first step is to make sure you have up-to-date antivirus protection and firewall software installed on your computer. Crypto ransomware will attempt to exploit vulnerabilities in your computer to install itself and begin encrypting your files.
If you have any doubts as to whether or not your computer is infected, you can use a malware removal tool such as SpyHunter to scan your computer for any malicious files or programs.
Once you have confirmed that your computer is infected, the next step is to remove the Crypto ransomware virus.
To remove Crypto ransomware virus using the most effective methods, we recommend using a malware removal tool such as SpyHunter. SpyHunter is a powerful tool that can remove all types of malware, including Crypto ransomware.
Once you have installed SpyHunter, run it and click on the “Scan” button to begin scanning your computer for the Crypto ransomware virus.
Once the scan is complete, SpyHunter will display a list of detected items. In order to remove the Crypto ransomware virus, please select the “Crypto ransomware” item and then click on the “Remove” button.
Please be aware that removing the Crypto ransomware virus may take some time, so please be patient while the tool works to remove the virus from your computer.
If you are still experiencing problems after following these steps, please contact our support team for help.